Syrian Electronic Army hackers: Who are they and why are they targeting the media
Hacktivist group relies on 'spear phishing' to deface media sites with its message

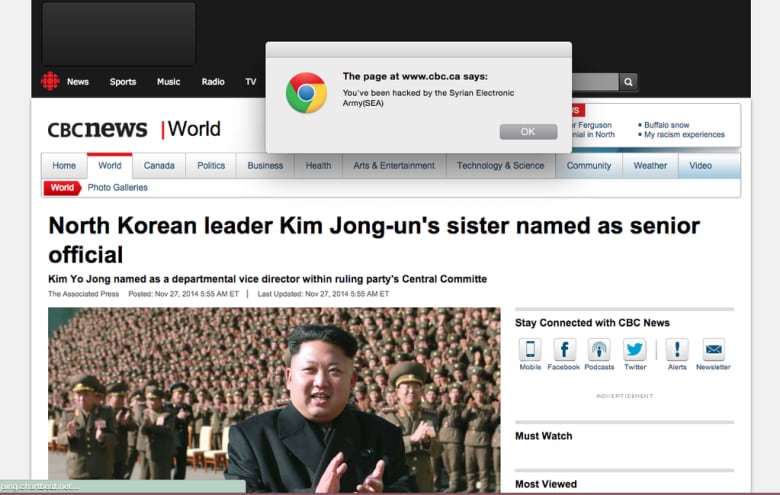
Yesterday morning, visitors to CBCNews.ca and other news websites around the world saw a pop-up message that read: "You've been hacked by the Syrian Electronic Army (SEA)."
The incident raised questions about who the group is, why it's targeting the media and just how dangerous it is.
What is the Syrian Electronic Army?
The Syrian Electronic Army is a hacktivist group that supports President Bashar al-Assad's regime in Syria.
Andrew Komarov, CEO of the Los Angeles-based cyber-threat intelligence company IntelCrawler, said he has been tracking the group's activities since it first surfaced in 2011, the year the country's civil war broke out, sparked by protests against al-Assad's regime.
He said the group is largely based out of specific universities in Syria, although it has members and contacts in other countries, including some linked to the Lebanon-based Islamist militant group Hezbollah. Based on the tracking of the group's financial statements, it has backing from Syrian government "entities" Komarov said.
The Syrian Electronic Army denies that it is under the orders of the Syrian government, but says it does forward information it obtains during the course of its activities to the Syrian government.
Who does it target with its attacks?
The group has two main targets, Komarov said:
- Media organizations, especially those in the U.S., which it uses for highly publicized attacks like today's.
- People linked to foreign governments and their military sectors, who are targets for cyberespionage — an activity that the SEA does not publicize.
Some of the group's past actions include:
- An attack on Reuters this past June, in which users who tried to view Reuters stories about Syria on a variety of news sites were redirected to a page that read: "Hacked by Syrian Electronic Army."
- Attacks on the Washington Post, CNN and Time and the New York Times in August 2013.
- A tweet sent out from The Associated Press Twitter account in April 2013 claiming there were two explosions in the White House and U.S. President Barack Obama was injured. That caused the Dow Jones index to lose more than one per cent of its value within 90 seconds.
Why is it attacking media organizations?
The SEA claims that its goal is "to show the truth about Syria." In an attack on Reuters earlier this year, it accused the organization of publishing "fake reports and false articles about Syria."
"It often comes down to trying to intimidate journalists who are saying anything bad against Bashar al-Assad," said Frederic Jacobs, a Swiss security researcher who has been following the activities of the Syrian Electronic Army as part of a project to study online censorship in Syria and Iran. "They believe that the Western narrative of the Syrian conflict is wrong."
One of the group's other main goals appears to be gaining publicity. Komarov noted that in one public interview, the group called itself the most famous hacking organization in the world.
How does it hack into media organizations?
Komarov and Jacobs agree that the SEA's attacks are technically not very advanced, but highly effective nonetheless.

The group is known for using the "spear phishing" technique, where employees at the targeted organization are tricked into providing their username and password. The SEA crafts fake emails that appear to come from a colleague, convincing the victim to log into a fake website that looks like a familiar site such as Google Docs.
Komarov said the SEA is "really professional," crafting convincing emails and "pretty and properly designed fake pages."
How does it hit multiple websites at once?
In some cases, the SEA's attack targets a company that offers web services to news organizations. For example, in the Reuters attack, it targeted Taboola, an online advertising network. In yesterday's attack, it hit Gigya, which provides a variety of services such as online advertising and tools for sharing news stories on social media.
Jacobs said many such services import a piece of javascript code that runs whenever someone visits the site of one of their clients, which may number in the hundreds — and can be used to execute malicious code.
How big a deal are the attacks?
Yesterday's attack was more of an embarrassment than a danger.
"I don't think it's done any damage," said William Buchanan, a computer security researcher at Edinburgh Napier University in Scotland, who has written about previous attacks by the SEA.
However, both he and Jacobs said the techniques used by the SEA could have been used to do more sinister things, such as bringing down services.
Komarov said that if spear phishing was indeed used, then someone's password was compromised, probably along with their email and access to software they work with, making them vulnerable to other crimes.
Jacobs said the SEA has done more damaging things in other attacks. For example, during an attack on Al-Jazeera, it searched for the names of Syrian people who were talking to the media, who then became vulnerable to persecution.
Jacobs thinks it's worrying that the SEA is often able to change the content of news websites. That means it could force visitors to download malware.
In other words, yesterday's attack may have been relatively benign, but it shows how vulnerable the targets are to more serious attacks.
How can businesses and users protect themselves from attacks?
Komarov recommends that organizations that can afford it use two-factor authentication, in which a second piece of identification, such as a card, needs to be used in addition to a password, making phishing ineffective.
Buchanan recommends educating employees about spear phishing and making sure a company's network defences and filters can detect phishing.
Jacobs said users can protect themselves from attacks like yesterday's simply by installing an ad blocking app. He recommends that those running websites reduce their risk by minimizing their use of services that execute code on their site.